WannaCry Ransomware Attack
In Harry Potter and the Deathly Hallows: Part 2, Voldemort and his followers stormed Hogwarts to capture Harry Potter. After much blood had been shed, Voldemort demanded Harry face him in the dark forest, or he would kill anyone who tried to conceal Harry from him.
Voldemort and his followers were lethal threats to everyone at Hogwarts, but I think there was a better way he could have drawn out Harry.
Voldemort should have employed a simple hostage takeover and demanded his followers to take hostages in Hogwarts until Harry surrendered himself to the dark lord.
Killing people obviously didn’t work because Harry kept on to find the remaining Horcruxes. But if Voldemort had cornered Harry by keeping all his followers hostage, he wouldn’t have had any help or time to find the Horcruxes, let alone destroy them.
Let’s carry on as if my scenario had happened because that is the basis of how the WannaCry ransomware attack happened.

What Is WannaCry Ransomware?
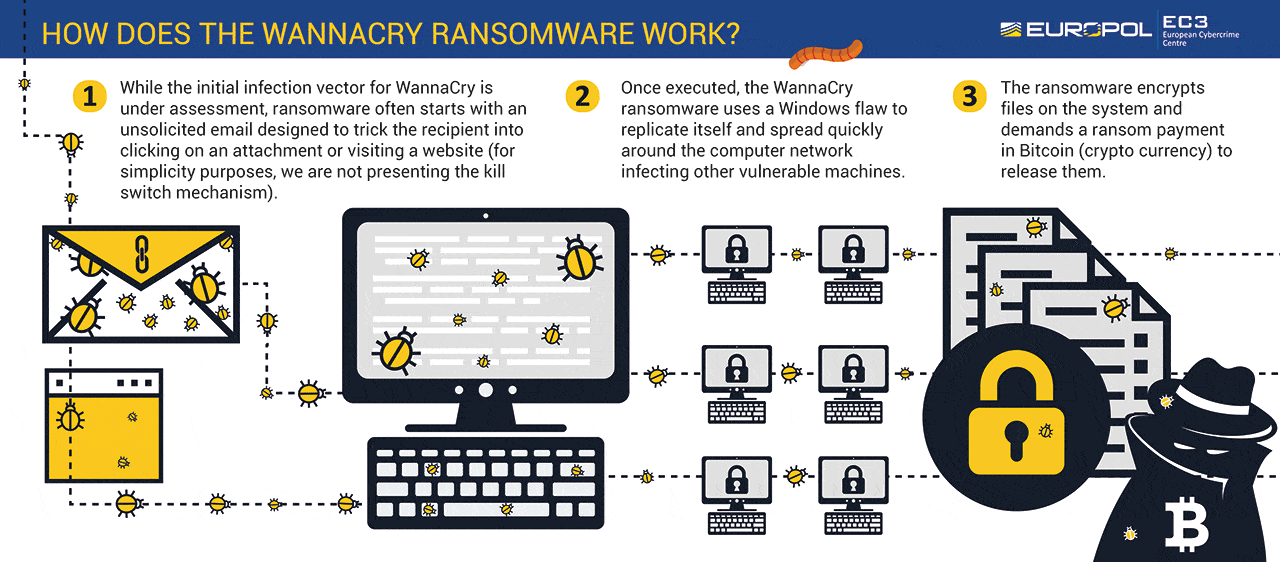
WannaCry ransomware was basically Voldemort and his followers attacking Windows operating systems in 2017, causing public panic and millions of dollars in loss. The WannaCry ransomware was malware that infected out-of-date Windows operating systems.
For anyone who wonders why Windows releases regular updates, this is why.
Each update puts another layer of protection on your operating system, patching up any hidden vulnerabilities.
Have you come across or heard of patch files? That’s what they do; they patch up loopholes that leave your system open to cyber threats.
When the WannaCry ransomware infected a PC, it locked and encrypted all files, and for users to regain access to those files, they had to pay Bitcoin ransoms in the amount of $300 or $600. However, there is no solid evidence that those who paid the ransom regained access to their data.
The WannaCry ransomware spread like wildfire because it was a worm, in essence. A worm is an entirely independent malware that can multiply itself without needing a host file. It means that WannaCry didn’t need to be activated by users; it used the system’s loopholes as gateways, got in, locked down the files, and then looked for ways to travel to another vulnerable system.
That’s why the WannaCry attack gained such a reputation and has been discussed up until now.
Back to my scenario about how Voldemort could have fished Harry out faster:
Think of Voldemort as the original WannaCry ransomware; although powerful and deadly, he couldn’t possibly pressure all of Harry’s followers – Windows operating systems – into giving him up. So the fastest way Voldemort could get to Harry was if he planted his followers in Hogwarts, which then they could hold everyone hostage until Harry gave up.
How Did WannaCry Ransomware Attack Happen?
The WannaCry ransomware attack couldn’t have happened without EternalBlue, a hacking tool developed by the US National Security Agency (NSA). A group of hackers known as Shadow Brokers found EternalBlue and released it online, making it accessible to everyone. The hackers behind the WannaCry attack used EternalBlue to launch the WannaCry ransomware attack on more than 200,000 PCs worldwide in just a few hours. (Voldemort would be pleased.)
Researcher Who Found WannaCry Vulnerability: Marcus Hutchins
Marcus Hutchins was a security researcher who was able to use advanced reverse engineering methods to stop the WannaCry ransomware attack to a huge degree. Marcus found the ransomware’s killswitch, which might never have existed if it wasn’t for the WannaCry vulnerability.
Damages of WannaCry Ransomware Attack
According to PCMag.com, the WannaCry ransomware attack affected Germany’s rail system, the UK’s National Health System (NHS), Renault and Nissan factories, FedEx, Spanish telco Telefonica, and Russia’s central bank. The worst damage was to hospitals as the staff couldn’t access medical files and had no choice but to cancel operations, putting patients in grave danger.

4 Tips to Combat WannaCry Ransomware & Other Malicious Threats
Whether it’s WannaCry, Petya, DoppelPaymer, REvil, SamSam, etc., there is always a cyber threat that can poison your system, steal or corrupt your data, or worse, lock you out completely. So here are simple steps you can take to reduce the risk of being a ransomware victim:
Pay Attention to Updates
Many users are basically allergic to updates. If you don’t install the latest security updates on your OS, your device becomes a fair game. Updates are necessary to keep your system vulnerabilities in check. So the next time you don’t install updates because you think they will slow down your system or whatnot, I want you to imagine that you’re creating hacker getaways all around your systems. Every update you ignore puts a smile on hackers’ faces.
Install Anti-Malware Software
I know we all hate to install additional software on our already loaded computers, but sometimes we don’t have a choice. Unless you are a security researcher like Marcus Hutchins and can monitor your system for security loopholes 24/7, which, let’s face it, no human can; you need to use security tools. It’s good to be cautious and not trust every cybersecurity software, but there are some you can and should trust. (Bitdefender is a great example of reputable, robust cybersecurity software that protects your device against all forms of threats. Instead of installing free and super unsafe security software, loosen the purse strings a little and invest in your system’s security. )
Back Up Regularly
When it comes to data security, you can’t ever be too careful; I will go as far as to say that it’s even good to be a little paranoid about it. Just because your data has been safe until now doesn’t mean it is shielded from cyber threats.
Hey, if you fire up your system and don’t connect to the internet, swell; don’t back up any data and carry on. (I can hear you saying: but everything is online!). That’s my point! Anyone at any time can penetrate your system and hijack your critical data, so why wait until it’s too late?

Elude Unknown Everything
Ransomware is crafty, especially the kind like the WannaCry ransomware that doesn’t depend on users’ actions to be activated; the only thing they need is a system loophole, and boom, your data become hackers’ paleta; delicious to taste and exploit.
WannaCry Ransomware FAQ
The WannaCry ransomware was powerful malware that targeted Windows operating systems to stop users from accessing their files. Once a PC got infected with WannaCry, all data would be encrypted and basically held hostage until the demanded ransom was paid. That’s why some people call WannaCry cryptoworm or ransomware.
The WannaCry ransomware attack happened because a hacker group called the Shadow Brokers released an NSA hacking tool called EternalBlue. EternalBlue is an exploit tool that enables WannaCry to infect Windows operating systems and lock down their data.
Marcus Hutchins, a brilliant security researcher, was able to use the WannaCry vulnerability to develop a killswitch that shielded many PCs from the WannaCry attack.
Yes. The WannaCry ransomware is still active and may never be fully neutralized. However, as long as you install Windows updates and use anti-malware software, you reduce the risk of losing your data to ransomware attacks.
Ransomware is like a weed; you cut one off, and two pop up the next day. But here’s a list of the most popular ransomware you should keep a lookout for:
-Locky
-Dharma
-Cerber
-BadRabbit
-BitPaymer
-NetWalker
-MeduzaLocker
-Cryptolocker
-GandCrab
-Maze
-NetWalker
-NotPetya
-Ryuk

0 Comments