Email Security Best Practices
I don’t know about you, but between the hackers and Meta’s data breach fiasco, I’m finding it hard to trust communication apps. But I can name one communication platform that has never let me down, email.
Now, you might think I am a cavewoman because I am putting email above giant communication platforms, but by the end of this article, you will feel differently.
However, because many businesses and organizations use email services to connect with their customers, hackers, and other cybercriminals have started to poke around in hopes of finding email security loopholes.
Before we get into email security risks, let’s discuss why people use email services.

Who Uses Email Services & Why?
Time for a fun movie reminiscence.
When I first saw the Harry Potter movies, one thing always excited me: the mysterious-looking letters Hogwarts sent to students. I would think, man, that’s a letter I want to read, even if it is a screaming one – the Howler – that Ron received from his mother after he stole the family’s flying car.
So can we agree that mails are a fun and convenient way of communicating with people? (I just wish emails looked as cool as Hogwarts letters. Someone may develop email holograms in the future, and then we can send and receive all kinds of magical letters.)
If you have a business, email services are the best and cheapest ways to keep in touch with your customers. You can tell them about your new products, promotions, holiday sales, etc., and anything you want to share about your business.
Individuals also use emails; it’s the most convenient communication platform, and everybody checks their inboxes at least once a day.
Also, have you noticed that when you sign up for a new platform, you are asked to put in your email address? Why do you think that is?
Great Potential of Email Inbox
Your inbox is the communication gateway no business can afford to miss.
Plus, as a user, you have all the power when it comes to emails; you can unsubscribe from any platform instantly, put suspicious senders in your spam folders, block certain people or companies, etc.

Now, as with any digital platform, there is a matter of security.
Granted that most reputable email providers like Gmail or Outlook use advanced protocols to ensure customers’ security, it doesn’t mean the cyber crooks won’t target them.
We don’t want to scare you, but if you are using a platform on a daily basis, then you need to make sure there aren’t any security loopholes that could get you in trouble.
You remain untouchable from those nasty cyber-attacks if you implement email security measures.
How to Prevent Email Threats?
The easiest email protection tool is to set your email settings only to receive text-only messages; this way, you won’t run the risk of clicking on phishing links or opening contaminated files.
But the issue with this email protection tool is that it’s too restrictive; most businesses exchange files as email attachments daily. So, we need an email security measure that doesn’t render the whole email communication useless.
Email Security Measures
Wouldn’t it be great if each of us had our own owls to carry our emails across the Internet safely? It would be much more awesome if we could cloak our owls to keep them hidden from prying eyes. (We would definitely need my favorite professor’s expertise in this matter_the, almighty Snape.) If Hogwarts approves of owls, then it’s good enough for me. 😀
Until someone creates email security owls, we need to take matters into our own hands.
Here are some tips to combat email threats:
Email Gateway Scans
To monitor ingoing and outgoing mail with advanced and multi-layered security protocols in order to spot malicious or spam messages.

Automated Email Encryption Solution
To encrypt sensitive emails before sending them to the recipients so they are shielded from snoopers. (Check out The Best Email Encryption Services for 2023 for more information.)
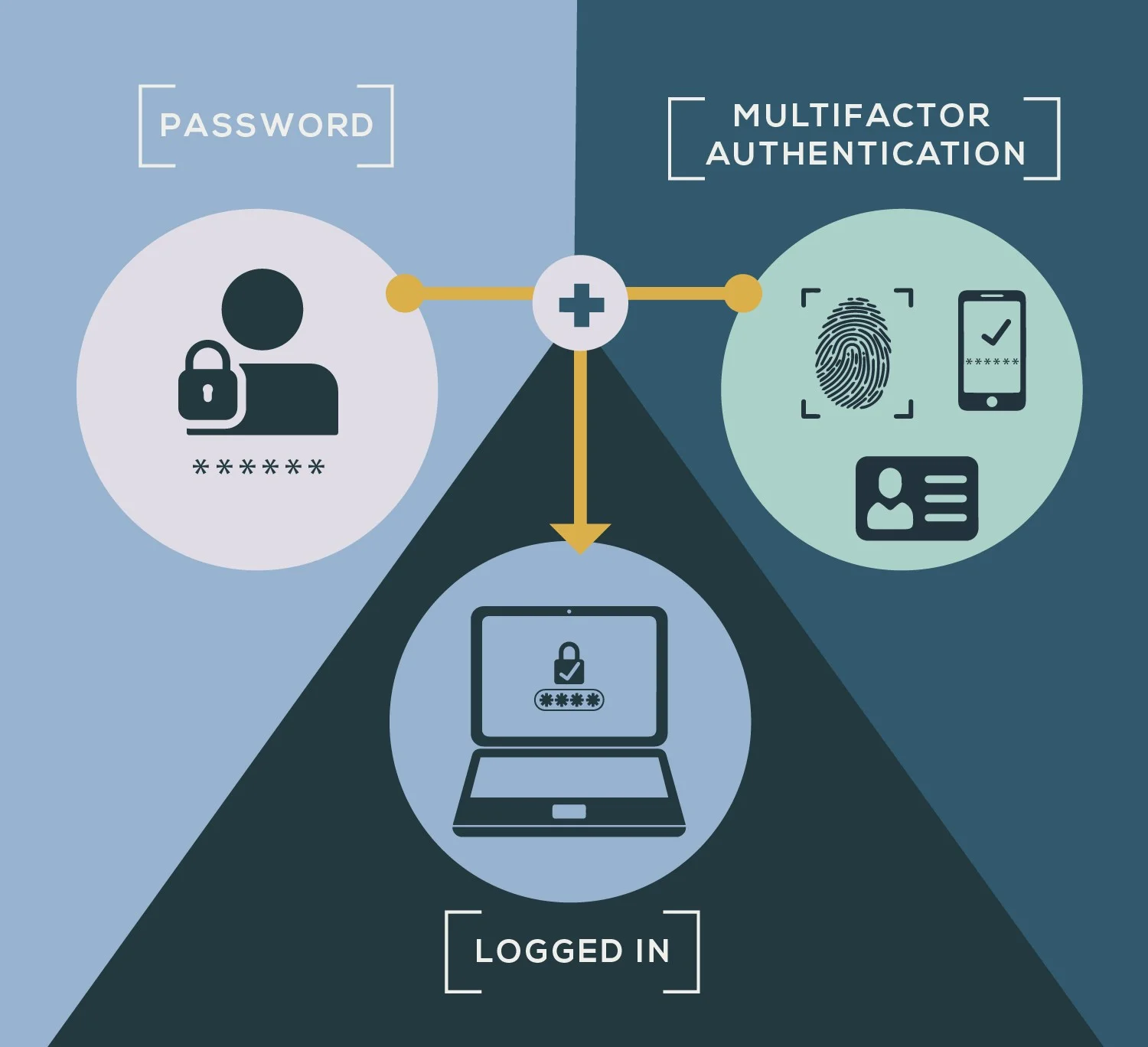
MFA (Multi-Factor Authentication) Methods
A necessary precaution to keep email accounts safe from hackers. (Keep in mind that MFA doesn’t work against phishing attacks if an account is already compromised.)
Encryption Add-ons/Platforms
To encrypt private emails containing sensitive attachments. (SendSafely, FlowCrypt, Cisco, and Virtru offer excellent encryption tools that neutralize most email security risks.)
Built-in Spam Filter
To separate legitimate email senders from fake ones and prevent phishing attacks.
Email Security Software
The best email protection tool against spoofing, phishing, and malware attacks. (Proofpoint, Avanan, Mimecast, Barracuda, and FireEye Email Laundry are great email security software you can use.)
In addition to all of these email security tools, remember to change your accounts’ passwords every six months or so. Also, avoid using weak passwords like 123456 or your birthday; you never know who is behind your email threats. It might be your high school friend who is always the first to wish you a happy birthday.
Different Types of Email Threats
You might think that a secure email gateway would solve all your email security issues. Still, as technology advances at a supersonic rate, email threats have become more sneaky. Most email threats are well camouflaged, especially to the average user’s eyes. But here are some of the more common ones to keep a lookout for:
Phishing:
Phishing scams are a means to bait people into clicking on malicious or fraudulent links. These kinds of emails have been around for a long time and have evolved in many troubling ways. One example is called spear phishing, in which specific individuals or groups are targeted.
The cyber crooks behind spear phishing attacks are after confidential or sensitive data like financial, medical, or legal information, especially information regarded as highly classified, like FBI or NSA databases. Extortion or brand impersonation are two more examples of spear phishing.
Another concept you should be familiar with is lateral phishing. Lateral phishing is about using already attacked or infiltrated accounts to attack other individuals within the same organization.

Unfortunately, as long as human workers are involved, companies run the risk of being victims of phishing campaigns. So if you have a business, make sure you educate your team on these super damaging email threats.
The best defense against spear phishing is to be 100% sure of the email sender’s identity before opening any email.
Domain/Identity Spoofing:
This is one of those well-camouflaged email threats that sneak through users’ systems very easily. Attackers set up bogus websites filled with dangerous malware and then cook up legitime looking domains to fool email recipients.
For example, you might get daily emails from Amazon, making you the perfect target for domain impersonators. Once they trick you into thinking the email you got is from Amazon, all it takes is a phishing message to gain access to your account information or, worse, customers’ details.
Big companies like Amazon, PayPal, eBay, Alibaba Group, etc., always use genuine email addresses, but cybercriminals are a crafty bunch and masterful at the art of disguise. So make sure the email you get is from a legitimate source before you click on anything or hand over any type of information.
BEC (Business Email Compromise) is an example of identity theft. The attacker gains access to the individual’s email account and poses as the account owner to extract confidential information from their contacts.
Spam:
Spam emails pair perfectly with phishing attacks. The hackers’ game here is to fill users’ inboxes with loads of useless or possibly infectious emails to overload the mail server. Each mail server can process a specific quota of messages daily, and when the pool is overflowing, nothing can get through. In the mayhem created by spam and junk mail, users can easily and absentmindedly click on malware-ridden links, and before they know it, the bad guys take their data hostage.

Email Threats Asking for Money
According to the FTC, some cybercriminals send chilling messages to email users asking for Bitcoin ransoms in exchange for keeping quiet about users’ online activity. In these sketchy messages, the attacker will probably inform you that they have hacked your webcam or installed tracking software into your system, tracing all your online activity. To make the deceit more believable, they reveal users’ old passwords in the malicious email, making users take hasty action to protect themselves.
Here’s what you should do, according to Malwarebytes CEO Marcin Kleczynski:
”First, have a healthy level of skepticism, then, remember, they almost certainly haven’t been recording you or have access to this type of information, if it even exists.”
So instead of panicking and paying up the hacker, report the incident to ReportFraud.ftc.gov or the FBI. Next, change all your passwords.
Top 10 Secure Email Providers
Choosing secure email providers is common sense if you have been aware of the rise of email threats over the past decades.
Gmail is one of the most popular and secure email providers we all know, but if they’re not your cup of tea, here is a list of other email providers you can use:
Outlook

Outlook is Microsoft’s secure mail service compatible with Windows and Mac operating systems. You can use Outlook for free or invest in Microsoft 365 Family for $97.12 annually.
Zoho
Zoho uses advanced security, monitoring, anti-intrusion, and prevention techniques to ensure data privacy. Its CRM is equipped with Advanced Encryption Standard (AES) to encrypt and decrypt users’ sensitive data.
AOL Mail
AOL Mail has gained popularity among users because it allows them to link their AOL accounts to their other email accounts, such as Gmail. As for convenience, AOL Mail is a good email provider. But if you link all your email accounts together, the rate of email security risks increases. So always make sure you use robust email security software or implement other security measures we discussed in the previous sections.

Mail.com
Mail.com is the perfect email service provider for businesses because of its excellent security features, such as a robust antivirus, spam filter, 2FA (Two-factor Authentication), TLS (Transport Layer Security), and more.
Thexyz
Thexyz is known for its 100% ad-free application that implements email protection protocols against viruses, malware, spam, and phishing ads.
Tutanota
If you are looking for an open-source secure mail service, Tutanota is the best option. Tutanota enforces end-to-end encryption and 2FA to protect users against common email threats.
ProtonMail
ProtonMail has gained a glowing reputation among secure email providers because of its zero-access architecture, meaning the company can’t ever access your emails. Also, Proton uses SPF, DKIM, and DMARC email security protocols to protect users against phishing and spoofing attacks.
GMX
GMX is a fairly safe email client that implements virus and spam protection protocols. But because they use pop-up ads, you should be extra careful not to click on suspicious-looking ones (I wouldn’t click on any because they might seem legit but can be linked to phishing websites).
CounterMail
CounterMail is well recognized for its OpenPGP encryption methods which ensure data safety to a considerable degree.
Hushmail
If you handle sensitive information in your business, such as legal or medical documents, Hushmail is the most secure mail service you can use. Hushmail ensures HIPAA-compliant data security and has a private message center.
Email Security Threats FAQ
Impersonation is probably the most dangerous email vulnerability. Domain spoofing is an impersonation technique used by cybercriminals to gain access to classified information within an organization.
Phishing, malware, and domain spoofing are the three musketeers of email threats. You can refer to ”Different Types of Email Threats” for more information.
All of the email threats we mentioned in this article can happen on phones and more. Because we use our phones for everything these days, and the screen is much smaller, phishing or spoofing emails are easily mistaken for legitimate ones.
According to prnewswire.com, impersonation attacks were the most common email threats that victimized IT and security organizations in 2022.

0 Comments