8 of the Most Common Cybersecurity Threats You Should Know About
In this article, we are going to take a look at what is considered today’s risk in the field of cybersecurity threats. Also, we will take a look at some statistics which have been provided.
In recent years, the Corona epidemic has been impressive in many fields. Regarding IT matters, it has had multiple consequences, including telecommuting development, changes in providing remote access, and even online systems growth. This has especially happened in government and organization services.
Cybercriminals have made optimal use of this option and have created considerable risks through these changes. More specifically, the risks that are somehow associated with workers’ telecommunicating.

In the next paragraphs, we note the cases cybercriminals have used in recent years. All are according to the reports of multiple reference websites. Many businesses and organizations have been harmed by it, both in the private sector and the governments.
1. Ransomware
Ransomware is a sort of malware that encrypts files and folders and doesn’t let the victim use them. Cybercriminals usually ask for money or cryptocurrency to make affected files and folders accessible.
In this regard, the computers of medical centers (for example hospitals) and the government sector have been exposed to a lot of damage from ransomware. These cybersecurity threats have increased during 2020 and 2021.
For instance, in 2021, according to some companies’ reports, the number of ransomware attacks directed at data leaks increased by 82% compared to 2020. To hide the cybercriminals’ identity, they use cryptocurrencies such as Bitcoin to receive their ransom.
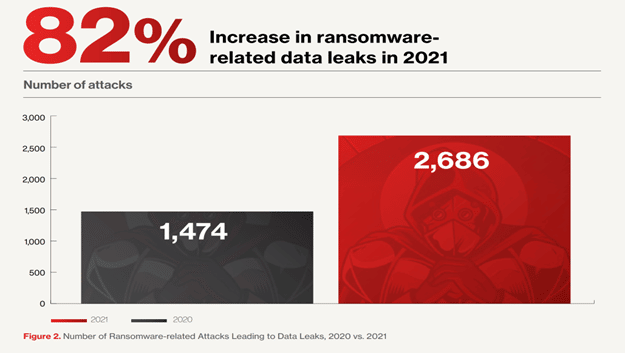
WannaCry, Cryptowall, and NotPetya are the most notable and infamous malware. In the following, you can see the name and risk level of some ransomware in 2021 registered by just one security company.
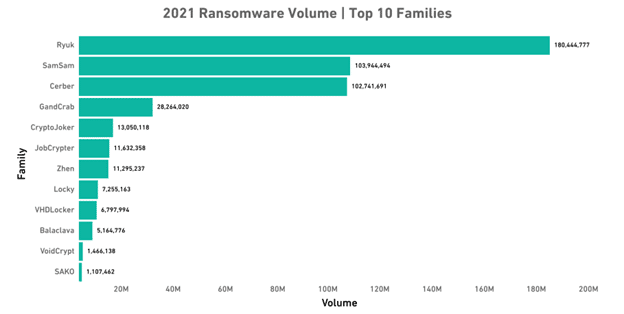
Although companies and organizations are always trying to keep themselves safe from ransomware attacks, some experts believe that hackers and cybercriminals are always ahead. This condition has made it very difficult to fight against this serious threat.
2. Supply Chain
This sort of cybersecurity threat is called a supply chain attack. That’s because instead of directly attacking a company, it infects the products and services such as software. Also, the product of a trusted business partner like the required software, or the libraries of that company have also been common targets.
A new era of supply chain attacks began when the American company SolarWinds announced that Orion, the company’s product, faced a supply chain attack in December 2020.
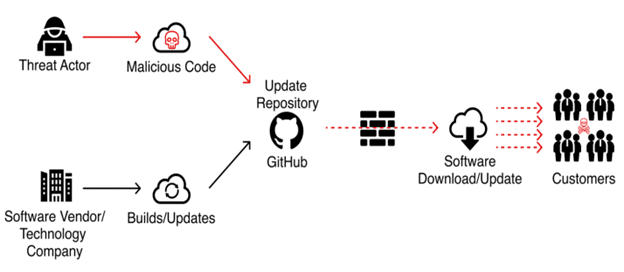
For instance, a risk based on the vulnerability of Log4j – a Java library usually available by default in all Java-based software – created many threats in 2021.
Similarly, on July 11, 2021, the Python package was found to contain infected and malicious codes. It happened when becoming available in the PyPI open-source code (the official repository of third-party Python software). This package had been downloaded 41,000 times!
3. CVEs Among Cybersecurity Threats
CVEs or Common Vulnerabilities and Exposures are actually unique identifiers that refer to a recognized vulnerability and risk in the technology field.
According to NIS statistics, more than 20,000 CVEs were recognized and published in 2021, happening for the first time in history.
This amount of vulnerability identification is not necessarily admirable by itself. On one hand, this number of identification shows the significant efforts of security companies in detecting these cybersecurity threats quickly and effectively. But it also shows that many destructive attempts have been made in this case to make so much work necessary.
One of the reasons for so many risks is that many companies and organizations prefer to use more software solutions and devices for security or their services. The more the number of devices and software, the greater the possibility of risks. In fact, the increase in the amount of hardware and software has multiplied the possibility of risks.
The following image is a list of the top 10 vulnerabilities in 2021:
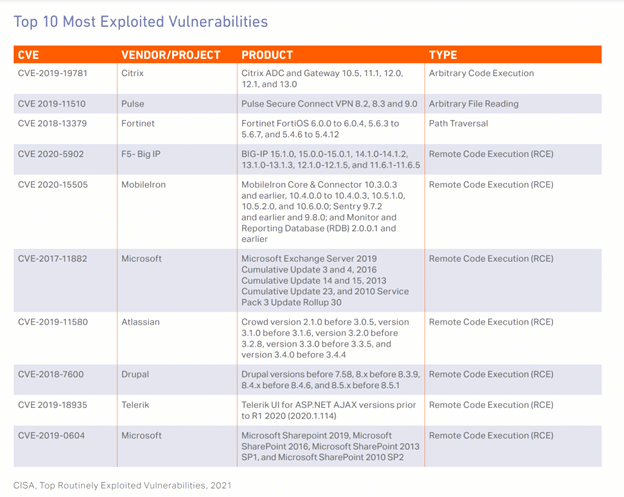
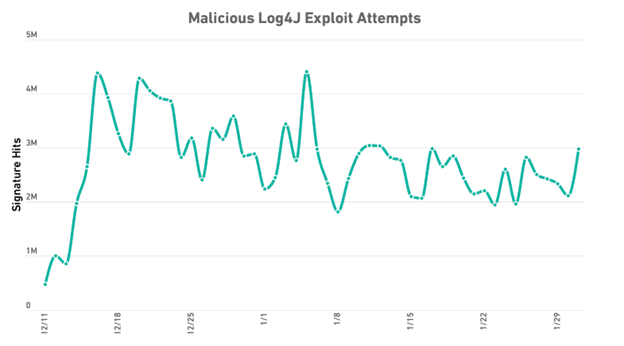
As an example, many exploits were created, and multiple attacks were registered when the Apache Log4j vulnerability was reported in 2021. Only one security company recorded more than 14 million exploit attempts in a 40-day period between December and the end of January.
Hackers’ and security criminals’ agility in this matter amazes us. As has been noted, just in the first 48 hours after release, the abusive attempts reached hundreds of thousands. Interestingly, on the third day, they exceeded more than 1 million.
4. Business Email Compromise
In these attacks, known as a kind of social engineering, businesses with several offices or enterprise partners in various zones have been mostly targeted.
The routine scenario of these cybersecurity threats is that cybercriminals copy and misuse the email accounts of high-level managers, executives, or financial officers. For the most part, hackers use the same email but with a domain very similar to the original one, or emails that seem to be the personal email of the administrators. They send an email to the employees and request them to pay some money as a donation or as a part of the company’s finances. In like fashion, hackers also use methods like keyloggers and phishing.
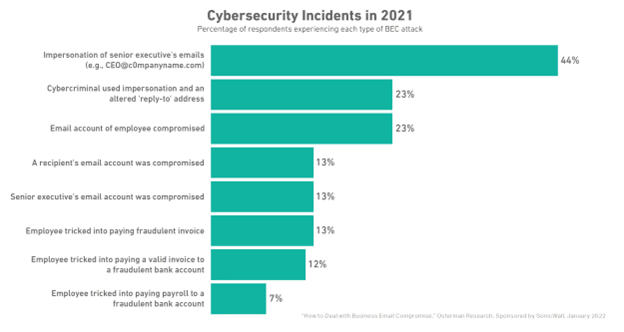
Despite their simplicity, these attacks are extremely intricate and have detrimental financial effects. According to the FBI, almost 20,000 of these attacks were reported to IC3 in 2021. The complainants lost an estimated $2.4 billion. This amount is very small in comparison with the global attacks. We should mention that these attacks have caused the greatest financial losses in the world, even more than ransomware.
5. Malware
The number of malware in 2021 maintained its multi-year decreasing trend, and it decreased by about 4% according to the report of a security company. This reduction is good news, but when we examine this monthly comparison with the prior year, there are some concerning signs. (Below image)
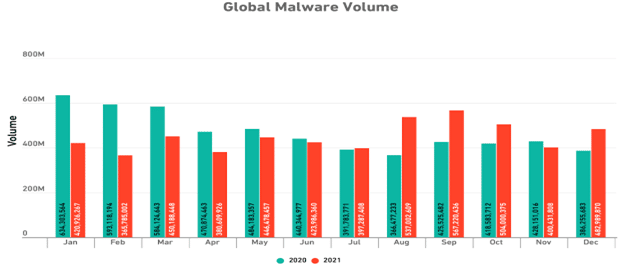
As we can see, this rate has increased in the second half of 2021 compared to the same rate in 2020. In terms of the amount of malware in geographical regions, during the years before 2021, the trend has always been downward. While this rate has reduced only in North America during 2021, in other regions, especially Europe and Asia, it has increased.
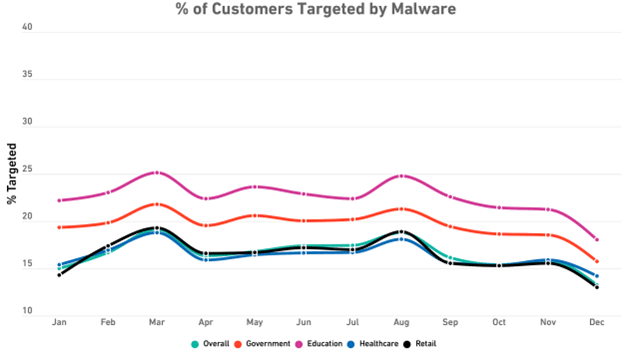
Regarding malware and its connection to the industry, the attacks in the health and government sectors are still the highest.
6. Cryptojacking
Cryptojacking is a cybercrime in which the resources of the victims’ systems are privately and illegally used to mine cryptocurrencies. This type of attack creates a cryptocurrency bot on the victim’s system or possibly uses the victim’s system and creates a botnet.
Usually, this happens by installing or running Cryptojacking software on the target’s system, or because the victim clicks on infected links in their email. It may occur through the JavaScript codes of an infected website that run automatically in the user’s browser.
In 2021, the rate of Cryptojacking attacks increased by 19% compared to the previous year, and cybercriminals’ attempts in this field reached 97 million.
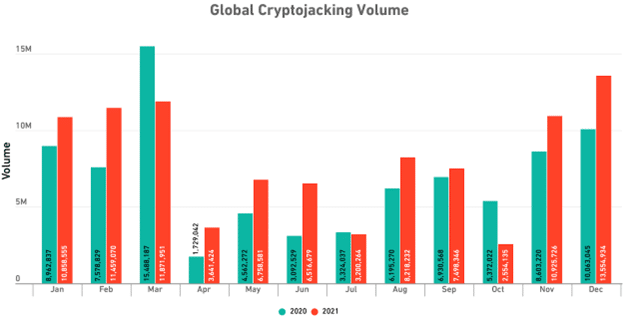
Although the record of such attacks was broken in 2021, significant growth happened in Europe. According to the estimate of one of the security companies, this increase was up to 60%.
In the last year, crypto-jacking has spread mainly through file-less malware, phishing attacks happening by malicious links, and also malvertising. Some crypto-jacking scripts even have the abilities of a worm and can spread themselves in the network.
In 2021, experts observed that criminals are distributing this kind of threat through other ways such as cracks, vulnerable web servers, and public hosting websites.
7. Encrypted Attacks Among Cybersecurity Threats
Encrypted attacks are a concept for all kinds of attacks transferred in an encrypted format to remain hidden from security products or people. They are also called encrypted threats. This includes all kinds of attacks such as malware, ransomware, and phishing.
In the internet world nowadays, experts use TLS (Transport Layer Security) and previously SSL (Secure Sockets Layer) to encrypt internet communication. For instance, you can see it in HTTPS or SFTP protocols.
As you know, this encryption makes the data undetectable along the way. This problem has caused cybercriminals to use these devices and encryptions to infect victims’ systems without being detected by security tools.
Other items include botnets. They use encryption for all activities such as communication, spreading, attacks, and other harmful actions to remain hidden. The most commonly used encryption attacks are found in ransomware when the victim’s personal files are held hostage through encryption.
Encrypted threat detection methods are complex. In some scenarios, experts use the traffic fingerprinting technique. It always monitors the network traffic path and checks if its activity pattern is similar to a threat or not. In other methods, IT experts use machine learning and behavior analysis algorithms to discover advanced techniques.
Firewalls and security equipment of the latest generation can identify such threats. So we should be ready to prepare them if necessary. According to many reports, the number of encrypted attacks in 2021 was more than the total amount in 2018, 2019, and 2020.
In the image below, you can see the rate of these attacks through HTTPS in different industry sectors.
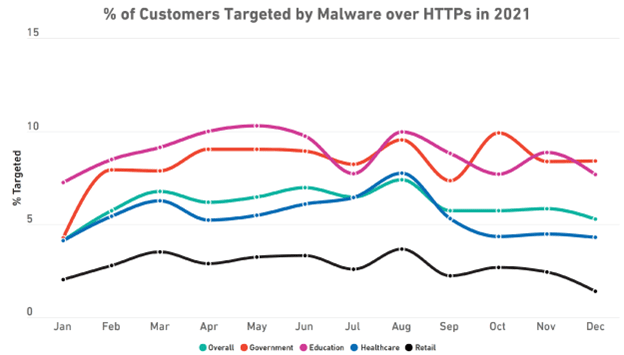
With that in mind, you should make sure your devices are equipped with up-to-date cybersecurity solutions. Also, it’s necessary to always update your antivirus solution to the latest version so that the database uses the latest algorithms.
8. Intrusion Attempt
An Intrusion Attempt is an attempt to infiltrate and harm through known cybersecurity threats and vulnerabilities (such as CVEs mentioned in this article). On the other hand, they may not have been appropriately identified or recorded yet, such as zero-day threats.
Even though these threats are recorded publicly, users and network administrators revise them in different time frames. Sometimes, they don’t even take any action. This is an opportunity for intruders, hackers, and cybercriminals to try to infiltrate systems and run their destructive activities.
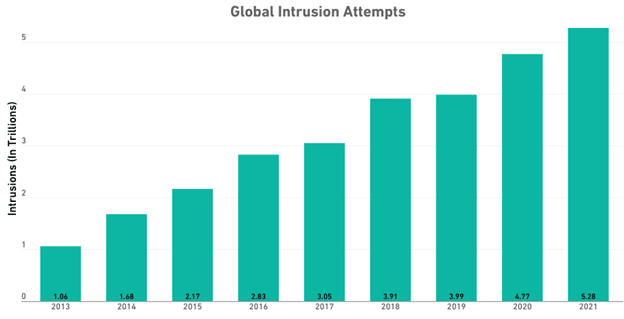
In 2021, just one of the security companies’ laboratories recorded nearly 5.28 billion intrusion attempts. This shows an increase of nearly 11% compared to 2020.
In recent years, the types of these attacks and their numbers have changed a lot. Below are the various types and the number of these kinds of intrusions.
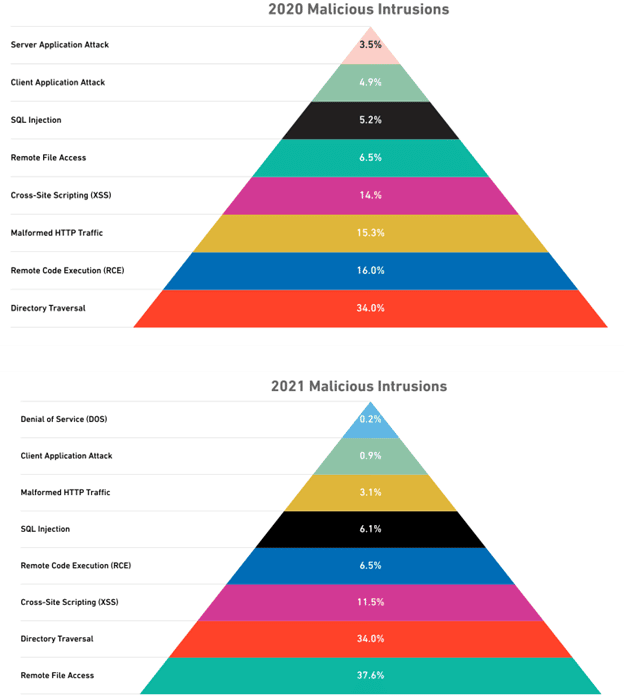
The most typical intrusion attempts among the cybersecurity threats are:
1. Remote File Access
It refers to the access of an unauthorized person to files and data that are only available to authorized persons.
2. Directory Traversal
It is a kind of attack in which the intruder gains access to files and folders outside their permissions. This attack allows the user to access programs or files more than what the system allows them to use.
3. Cross-Site Scripting (XSS)
It is a kind of code injection on the client side. Usually, when the client opens an infected web page or application, they run malicious codes (mostly JavaScript codes). They transfer malicious scripts to the victim’s web browser or software to get the required information or perform specific operations.
4. Remote Code Execution (RCE)
An RCE attack happens when a cybercriminal uses a vulnerability and remotely executes a malicious code on a user’s system with high accessibility.
5. SQL Injection
This attack happens when cybercriminals inject a malicious SQL statement into a vulnerable application or website. They gain access to basic database information by doing so.
6. Malformed HTTP Traffic
It refers to patterns or shreds of evidence that will not be found in a valid HTTP request or response. For example, changing the HTTP header size.
7. Client-Application Attack
In this type of attack, the users’ own programs are attacked directly. For example, memory leaks.
8. Denial of Service
In Dos or DDOS attacks, the goal is to prevent a service provider (e.g. a website) from providing service properly and completely. It usually happens by sending a large amount of data to the server.
In DDOS attacks, which are more common, hackers or cyber criminals carry them out from several sources. Doing so to makes it more difficult for the victim to detect and block.
9. Malicious PDF and Office files
In recent years, using malicious files in PDF format, along with Microsoft Office files, has become common among cybersecurity threats. The data of a security company’s laboratories have reported an increase of almost 52% for pdf and 64% for office files.
It’s worth mentioning that the recent observations of the same company show a significant decrease in the interest of hackers and cybercriminals in using PDF files. Alternatively, they have moved towards using Office documents. These attacks were not limited to attacking and removing users’ files since other methods were also used.
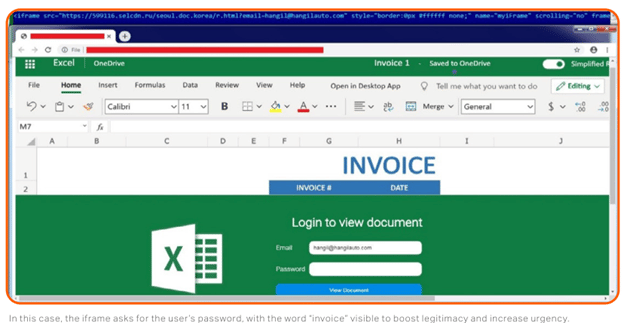
For example, in the image above, hackers have requested the victim to enter his Microsoft credentials to view the invoice. In fact, in this kind of phishing attack, the goal is to get the victim’s user information on Microsoft’s website.
10. IoT Malware
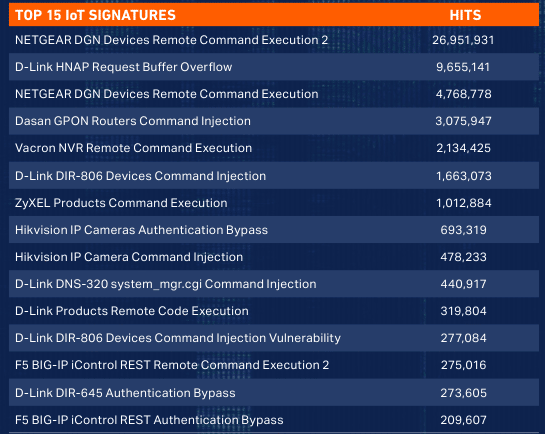
The Internet of Things has been very popular in recent years. Many businesses have used it, and predictions indicate a larger market share in the future.
According to IDC, there will be 55.7 billion IoT devices by 2025. The highest number of attacks in this category has been related to routers, cameras, and their storage devices (NVR). In the image below, you can see some of these tools that have caused high risks.
Summary of the Most Common Cybersecurity Threats
In recent years, the methods of cybercriminals have developed so much, making it difficult to identify and protect yourself against their attacks.
The thought-provoking reason for increasing the level of cybersecurity threats is the growth in the level of attacks. Due to the increase in risks, companies and individuals always try to put more security equipment and software into use. The same conditions apply to Internet of Things (IoT) equipment.
In fact, this is inevitable. But the issue is that by providing these tools, the probability of risks and bugs in these companies increases. It has created a cycle that seems to be in favor of cyber criminals and hackers. Experts suggest considering maximum accuracy in adding tools and systems to the groups and companies to minimize additions.

Moreover, you should consider the increase in the awareness level of the end-users regarding the current risks. Although more security devices are available, a considerable amount of the risks depend on the end users’ awareness. Consequently, everyone should make more efforts in this regard.
Bitdefender has proved to be a reliable solution to fight against ransomware attacks, malware, intrusions, email threats, etc. for consecutive years according to various test results. You can easily secure your devices with Bitdefender products, whether you use Windows, MAC, Android, or iOS.
Get started today and guarantee your immunity from all threatening acts of the digital world.

0 Comments