Computer Viruses: How They Work and How to Prevent Them
When there’s talk about viruses, I cannot help but think of Fringe.
Before watching Fringe, I thought I knew about pretty much all common viruses, but boy, was I wrong. For those unfamiliar with Fringe, it was a television series involving FBI special agent Olivia Dunham, a brilliant doctor Walter Bishop, and his son Peter.
The show was about solving weird FBI cases revolving around Fringe science, Dr. Bishop’s area of expertise. From mutated cold viruses, the rapid skin growth toxin, and the worm virus (Snakehead), we saw it all in Fringe.
Most of the time, viruses are harmless, and the body can counteract them with treatment. But the viruses in Fringe were exceptional examples of how deadly a virus can be.
Whether it’s a human virus or a digital virus, you must deal with it. Otherwise, the number of casualties would skyrocket.

In this article, we want to talk about computer viruses. We can’t see computer viruses with our eyes, so they are sort of invisible but hugely problematic.
Let’s get a bit more technical.
What Are Computer Viruses? The Simplest Definition
Computer viruses are malicious and infectious software or programs that infiltrate computers to sabotage, corrupt, or even steal data. Just like a human virus that can replicate itself inside the body and is usually contagious, once computer viruses set up camp in your system, your whole system and everything connected to it is at risk.
Computer viruses are malicious codes that:
- Disrupt systems’ resources (such as reformatting the hard drive or rerouting networks)
- Corrupt, delete, or steal data
- Corrupt software and applications

Different Types of Computer Viruses
Like human viruses, computer viruses come in many forms (I’m so glad they are in code form, aren’t you?) and are constantly evolving. But some common types of computer viruses are:
- Resident virus: A resident virus is a malicious resident in your system’s memory. Depending on its coding, this virus infects any system operation connected to your RAM.
- Multipartite virus: This virus targets your system’s hard drive and infects the boot sector and executable files. Since it does all the essential computing on the hard drive, this type of virus can cause severe damage to your whole system. Remember that Multipartite viruses can replicate themselves very fast_hence their name.
- Direct action virus: This is sort of like a snipper virus; it goes after specific targets, infects, replicates, and destroys. This type of virus mostly goes after executable files. Once it executes the files, the virus spreads like wildfire. (Direct action virus is also called a non-resident virus.)
- Browser hijacker: This type of virus alters your web browser settings without you noticing. Once this virus steps in, it can open the door to other malicious software like adware, keyloggers, spyware, etc.
- Overwrite virus: This type of virus hates original program codes and replaces them with its own malicious code. Once the malicious codes are in place, the virus spreads through the system and network.
- Web scripting virus: This virus is a more advanced version of the browser hijacker virus; it exploits your web browser’s vulnerabilities, changes its security settings, and even brings down the webpage. Web scripting virus usually hides in pop-up ads or other infected links.
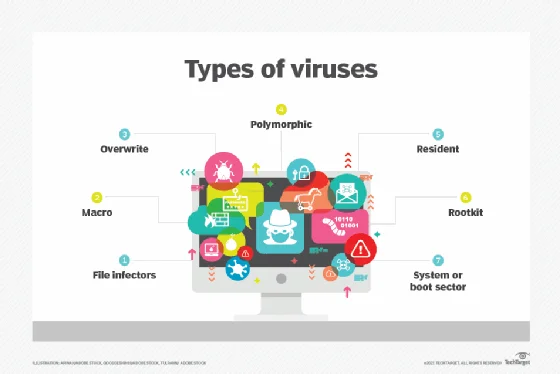
- File infector virus: This type of virus goes after executable files, corrupting or damaging them so that other programs start to malfunction when the user runs them. The file infector virus sets up shop in your system’s memory, and even after the infection spreads, it remains active to infect any new program or file.
- Network virus: This type of virus goes after networks and multiplies itself through the network packet, infecting any computer connected to the network. (Some call the network virus a network worm as well.)
- Logic bomb virus: Also known as time bomb virus, it is embedded in a program as a set of instructions waiting to be activated by the right conditions. It’s like an actual time bomb set to go off under specific circumstances. (Like the one David Robert Jones used to activate Olivia’s ability in Fringe_yes, I love Fringe analogies, sue me. 🙂)
- Trojan Horse virus: This type of virus is the disguiser in the virus land; it disguises itself as legitimate, legal software to infiltrate systems. Although we listed Trojan Horse as a virus, according to Malwarebytes, it’s actually malware. (If you don’t know the difference between a virus and malware, click here.)
- Macro virus: This type of virus is written in macro, a common programing language. It is usually hidden in word-processing software like Microsoft Word. Hackers can also embed the Macro virus in documents, so email attachments can easily contain it. So by opening the files, they infect your whole system.
I think it’s a good thing we cannot actually see computer viruses; imagine they were like the mutated cold virus in Fringe; how gross was that? (In case you didn’t watch Fringe, the mutated cold virus was a huge virus that clawed itself out of the body through the throat.)
But picturing computer viruses as slimy and fast viruses might help you want to take action against them. So, in this case, fear is a good thing. In the upcoming sections, we will give you helpful tips to combat computer viruses like a fierce ninja. So stay tuned.
How Do Computer Viruses Spread?
Computer viruses can spread in three ways:
- Computer to computer
- Through a network
- Through digital devices (USB, hard drives, etc.)
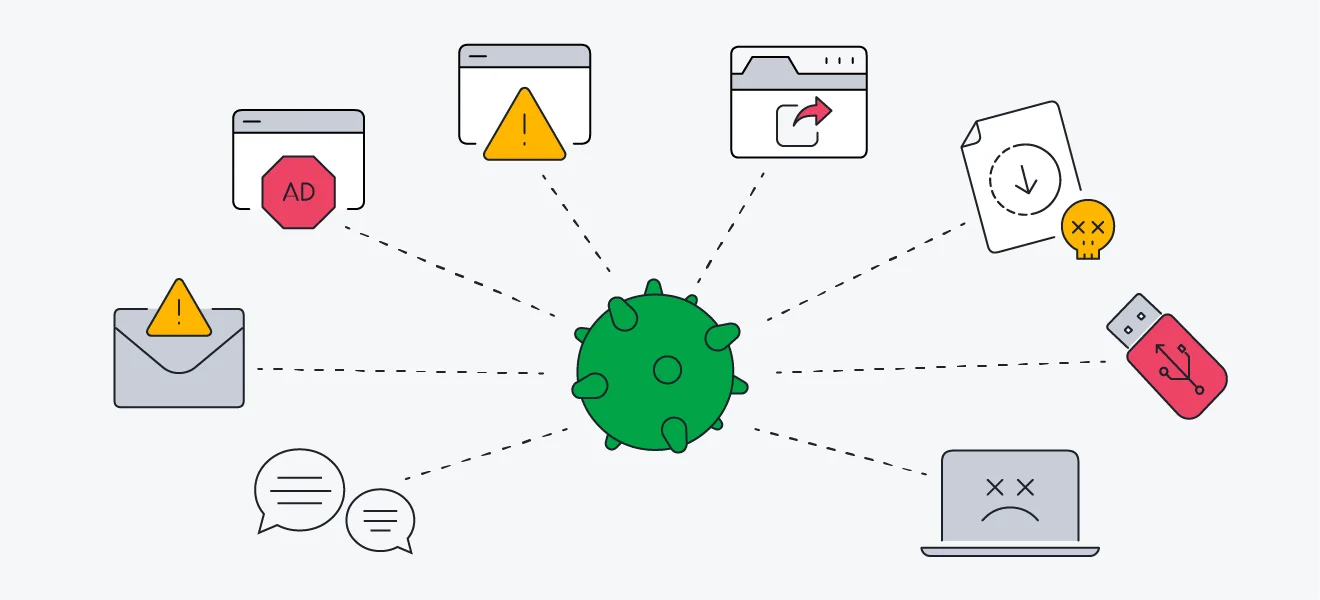
The first and third way computer viruses spread is pretty self-explanatory, but the second way, which is the most dangerous, deserves more explanation.
Everything is connected to the internet, which is both good and bad. It’s good because everything is much more accessible this way, and bad for the same reason. Once something is easily accessible, it becomes vulnerable.
Computer viruses can bounce through a network and infect systems, emails, web pages, programs, applications, software, etc. Pop-up ads/banners are the easiest and most effective camouflage for computer viruses because the chances of users clicking on them are quite high.
The Impact of Computer Viruses on Personal & Business Computing
Computer viruses or malware are merciless attackers, infiltrating and taking the spoils without leaving a footprint. Whether you run a business or not, computer malware can inflict million-dollar damages to your system.
Imagine you run a legal or healthcare organization handling sensitive and confidential data. If your system gets attacked or infected by computer malware, your data will be deleted or corrupted. Even worse, hackers might force you to pay a hefty ransom to regain access to them. (That’s how ransomware works; it takes your data hostage by encrypting it and doesn’t release it until you pay the ransom.)

If a company loses its customers’ data, its reputation will be tarnished. Also, the owner could be fined millions of dollars, leading him to bankruptcy.
Now if you don’t have a business and think no worm or hacker will come after your seemingly unimportant data, think again. Read this article from cnet.com, and you will know what we’re talking about.
10 Famous Computer Viruses in History
Here’s a list of notorious computer viruses that have caused many individuals and businesses severe damage:
- ILoveYou: A malicious virus that was embedded in an email attachment. The said email looked like a love letter, and once the recipient clicked on the attachment, the virus sent itself to all of the recipient’s email contacts.
- Sasser: A malicious worm that targeted Microsoft operating systems Windows XP and Windows 2000 in 2004. According to Theguardian.com, the Sasser worm infected between 2,000 and 1m computers, including Britain’s Maritime and Coastguard Agency.
- Nimda: A computer worm that targeted internet traffic and caused DDoS attacks.
- Chernobyl (CIH): This virus was basically an overwrite virus that targeted Microsoft systems in 1998. The CIH virus also corrupted the basic input/output system (BIOS).

- SirCam: A computer worm surfaced in 2001 and spread through Microsoft systems through an email attachment.
- Melissa: A macro virus that targeted Microsoft Word and Outlook-based systems and spread quickly by replicating itself through an infected email.
- CryptoLocker: A ransomware embedded in email attachments and, once opened, took over system files and encrypted them.
- MyDoom: A virus that infected Microsoft systems through emails. The main purpose of the virus was to launch DDoS attacks which it did on major companies, including Google and SCO.

- Storm Worm: A Trojan Horse virus that was hidden in email attachments. Once the recipient opened the attachments, the virus created a backdoor in the computer that enabled the system’s remote control access for outsiders.
- Conficker: A computer worm that targeted Windows systems and infected executable files while running as an invisible application in the background.
Microsoft is the most popular and easy-to-use operating system, which makes it a great target for malicious cyber attacks. So if your device runs on Windows, it’s essential to use a robust computer antivirus to prevent severe damage from ever-evolving computer viruses.
(According to Forbes.com, Bitdefender is one of the top antivirus solutions on the market.)
How to Know if a Computer Is Infected? (Signs of an Infected Device)
There are many ways you can tell whether your system is infected by a worm or computer malware:
- Your desktop background keeps changing on its own.
- Some of your web browser settings change without your authorization.
- Your outbox is filled with emails you did not send.
- Your files or programs open or close suddenly without you clicking on any button.
- Your keyboard keys get clicked randomly.
- The applications or software you frequently use malfunctions, show unusual errors, or log you out.
- Unwanted pop-up ads keep reappearing on your browsers or homepage.
- Some system applications won’t open or load.
- Sluggish system performance.
- Internet connection issues.

Any kind of unusual system activity is indeed a good reason to take a look at your computer antivirus. If you don’t have one, then it’s time to get the most affordable and ruthless antivirus: Bitdefender.
Bitdefender is one of the most renowned antivirus and cyber security solutions on the market, which can surely protect you against computer viruses. The Bitdefender team is all about threat prevention, so they are always adding new security features to their products like AntiRansomware Remediation.
The Future of Virus Protection & Prevention
“We need a multilayered autonomous plus a managed solution,” says Forbes.com.
The best protection against computer viruses, malware, worms, and other types of cyber threats is to secure every loophole within our devices and also the internet. A robust computer antivirus like Bitdefender can help you with both.
As cyber threats evolve, we need to enforce extra layers of security to protect our personal and business data. With Bitdefender, you will always be one step ahead of cyber criminals and malicious attacks. Investing in such a powerful cybersecurity solution is not an option; it’s a necessity.
Secure your best deal here.
Tips for Staying Safe Online & Avoiding Viruses
Some of these tips are common sense, but we will list them just in case:
- Invest in a trustworthy and effective cybersecurity solution like Bitdefender.
- Set strong passwords for all your accounts; do not share them with anyone.
- Do not click on any suspicious ads.
- Do not open emails from unknown senders. Sometimes the email sender’s address might look legit, but in reality, it’s a product of domain/identity spoofing. (Click here to learn more about email threats.)
- Do not use public Wi-Fi.
- Update your operating system.
- Do not install programs from unknown application stores.
- Do not click on random links.
- Use a trustworthy VPN.
- Do not download suspicious or weirdly-named files.
- Do not buy anything from shady websites.
- Look out for fake social media profiles and refrain from talking to strangers.

Remember that any system vulnerability attracts computer viruses like moths to a flame. So make sure you shield your system against cyber attacks properly.
Final Thoughts
The online world has become our second and sometimes even our first world. We are all on our phones and laptops doing all sorts of online activity all day long, which is great but leaves us open to malicious cyber attacks.
It takes only one mistake to invite the bad guys to your system; clicking on unfamiliar or shady-looking links, opening emails from unknown senders, executing infected files, etc.
To protect yourself and your system, you need to shoot first and ask questions later. In other words, you let your antivirus solution quarantine a threat (one of the many security features of Bitdefender) and then examine the situation.
Just like human viruses, computer viruses, if not contained, can surely cause irreversible damage to your system. Keep your eyes open for the signs of an infected system we mentioned here, and in the meantime, install Bitdefender to close the gates on any unforeseen cyber threats.
Computer Viruses Guide FAQ
Computer viruses are malicious software or codes embedded in systems, files, applications, web pages, etc. Most computer viruses are well hidden on digital devices. But quietly and rapidly, they replicate themselves to infect the whole system.
Shoot first; ask questions later, which means that you need to install a powerful computer antivirus on your device and let it annihilate any cyber threat upon detection. Sometimes an antivirus might flag a legitimate program as a virus and quarantine it (as Bitdefender does), but that’s not an issue. You can examine the threats and take action accordingly, but it’s always better to be safe than sorry.
Sudden changes in web browser settings.
Sluggish system or apps performance
Outbox filled with emails you didn’t send.
Unwanted pop-up ads.
Check out the “Signs of An Infected Device” section for more information.

0 Comments